Enhance your systems with advanced cybersecurity solutions
Threat Pulse Packages
SIEM & EDR
Security Information & Event Management (SIEM):
- Log Collection: Gathers logs for analysis
- Event Correlation: Links events to detect security incidents
- Threat Detection: Uses advanced analysis to spot threats
- Real-Time Monitoring: Monitors logs and detects suspicious activity in real-time
- Compliance Reporting: Produces reports for regulatory compliance
Endpoint Detection & Managed Response:
- Threat Intelligence: Identifies threats through data and behavior analysis
- Automated Response: Quickly neutralizes threats, minimizing downtime
- Incident Response: Swiftly manages and contains incidents
- Advanced Reporting: Management reporting with detailed security insights
Threat Hunting & Correlation:
- Cross-System Correlation: Links events for comprehensive security
- Behavioral Analysis: Identifies patterns in user and system behavior
- Advanced Detection Models: Uses machine learning for threat detection
- Proactive Threat Hunting: Actively searches for hidden threats
- Indicators of Compromise: Identifies known attack indicators
Real-Time Alert Detection & Notification:
- Real Time Response Triggers: Activates immediate response actions
- Automated Threat Scoring: Assesses risk levels in real time
- Automated Alerts: Issues instant alerts based on set thresholds
- Custom Alerts Rules: Allows personalized alert criteria

SIEM Essentials
Price: Custom Quote
(based on no. of systems/daily data ingestion)
Setup Fee: Determined based on deployment scale

EDR Protection Pack
Price: Custom Quote
(based on no. of systems/daily data ingestion)
Setup Fee: Determined based on deployment scale

Comprehensive SIEM & EDR Solution
Price: Custom Quote
(based on no. of systems/daily data ingestion)
Setup Fee: Determined based on deployment scale

Add-ons: Ongoing Management & Maintenance (Custom Quote)

Log Management Center
Manage your logs seamlessly and access real-time analytics with fully customizable views on the Trust-OS SOC Dashboard
- Log Management & Centralization: Streamline log data for compliance, analysis, and incident response
- Centralized Log Collection: From all systems to one place
- Log Normalization: Formats logs for unified analysis
- Log Storage: Retains logs for compliance and analysis
- Log Search: Provides tools for in-depth log searches
- Log Rotation & Retention: Manages log storage efficiently
________________________________________
- Distributed Log Ingestion: Manage security incidents and insights through an interactive dashboard
- Scalable Collection: Ingests logs from multiple locations
- Decentralized Logging: Collects logs from remote environments
- Log Aggregation: Combines logs for centralized analysis
- Multi-Platform Integration: Integrates logs from various platforms
ENHANCE YOUR LOG MANAGEMENT CAPABILITIES
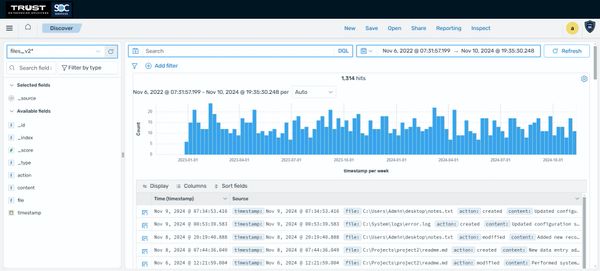
Real-Time Log Analysis
- Real-Time Correlation: Correlates logs across systems to identify potential threats
- Anomaly Detection: Detects unusual behavior in systems or application
- Alert Generation: Issues alerts based on suspicious patterns
- Trend Analysis: Analyzes trends to predict future security incidents
- Custom Reporting: Generates reports tailored to your business needs
E-Commerce Log Management
- E-commerce Transaction Monitoring: Monitors e-commerce transactions for suspicious activity.
- E-commerce Website Log Analysis: Analyzes logs from e-commerce platforms for performance and security insights
- Customer Behavior Analytics: Provides insights into customer activities for marketing and security
- Fraud Detection: Identifies and prevents fraudulent transactions

Log Management Essentials
Price: Custom Quote
(based on no. of systems/daily data ingestion)
Setup Fee: Determined based on deployment scale

Advanced Log Management Center
Price: Custom Quote
(based on no. of systems/daily data ingestion)
Setup Fee: Determined based on deployment scale
Flexible contract terms ( 3 / 6 / 12 months ) - up to 20% savings on annual terms!
Flexible contract terms ( 3 / 6 / 12 months ) - up to 20% savings on annual terms!
Flexible contract terms ( 3 / 6 / 12 months ) - up to 20% savings on annual terms!
Flexible contract terms ( 3 / 6 / 12 months ) - up to 20% savings on annual terms!
Flexible contract terms ( 3 / 6 / 12 months ) - up to 20% savings on annual terms!
Flexible contract terms ( 3 / 6 / 12 months ) - up to 20% savings on annual terms!

E-Commerce Log Management Pack
Price: Custom Quote
(based on no. of systems/daily data ingestion)
Setup Fee: Determined based on deployment scale
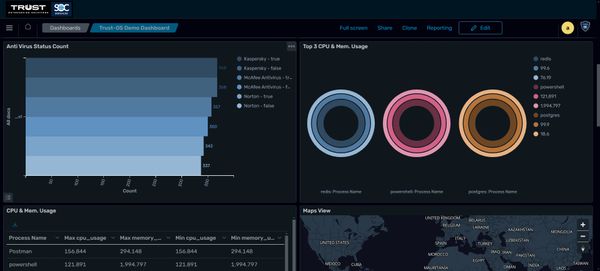
SOC Security Analytics Dashboard
- Send Vulnerability Scans / Penetration test requests to receive detailed reporting on your systems/networks
- Real-time threat monitoring with alert notifications
- Customizable views to select preference of analytics display
Available with all Threat Pulse packages! Book a free demo
Full THREAT PULSE PACK
SIEM Essentials + EDR Protection Pack
- Log Collection - Event Correlation - Threat Detection - Real-Time Monitoring - Compliance Reporting - Monitoring Alerts - Threat Intelligence - Automated Response - Incident Response - Advanced Reporting
Threat Hunting & Correlation
Cross-System Correlation - Behavioral Analysis - Advanced Detection Models - Proactive Threat Hunting - Indicators of Compromise
Log Management Center
- Centralized Log Collection - Log Normalization - Log Storage - Log Search - Log Rotation & Retention
Distributed Log Ingestion: Scalable Collection - Decentralized Logging - Log Aggregation - Multi-Platform Integration - Trend Analysis
Real-Time Log Analysis: - Real-Time Correlation - Anomaly Detection - Alert Generation - Trend Analysis - Custom Reporting
Expert SOC Consultancy
Schedule a free consultation to assess your business's cybersecurity needs. Our SOC specialists are ready to enhance your current security operations or build a comprehensive, tailor-made cybersecurity system from the ground up!
Trust Outsourcing Solutions
Copyright © 2023 Trust Outsourcing Solutions - All Rights Reserved. - terms & conditions / Privacy Policy